NSA targets the privacy-conscious
The rules related to Tails clearly demonstrate how easily web searches and website visits can be spied on by XKeyscore. On June 25, 2014, the United States Supreme Court noted how sensitive this type of information is in their Riley v. California decision against warrantless searches of mobile phones: "An Internet search and browsing history [...] could reveal an individual’s private interests or concerns - perhaps a search for certain symptoms of disease, coupled with frequent visits to WebMD."
In addition to anonymous internet access, Tor also provides a mechanism for hosting anonymous internet services called "Hidden Services". These sites' URLs contain a domain name in the pseudo-top-level-domain ".onion" which is only accessible using Tor. The code shown below finds and catalogs URLs for these sites which XKeyscore sees in "raw traffic", creating a unique fingerprint for each onion address. Each .onion address found in raw traffic is extracted and stored in an NSA database:
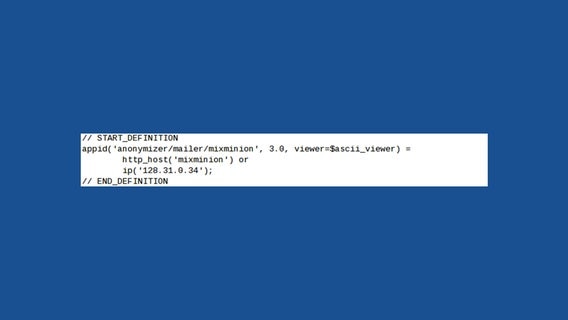
There are also rules that target users of numerous other privacy-focused internet services, including HotSpotShield, FreeNet, Centurian, FreeProxies.org, MegaProxy, privacy.li and an anonymous email service called MixMinion as well as its predecessor MixMaster. The appid rule for MixMinion is extremely broad as it matches all traffic to or from the IP address 128.31.0.34, a server located on the MIT campus.
That server is operated by the Tor Project's leader Roger Dingledine, an MIT alumnus. The machine at this IP address provides many services besides MixMinion, and it is also one of the above-mentioned Tor directory authorities. Dingledine said "That computer hosts many websites, ranging from open source gaming libraries to the Privacy Enhancing Technologies Symposium website."
Sebastian Hahn, the Tor volunteer who runs Gabelmoo, was stunned to learn that his hobby could interest the NSA: "This shows that Tor is working well enough that Tor has become a target for the intelligence services. For me this means that I will definitely go ahead with the project.”
When asked for a reaction to the findings, the Tor Project's Roger Dingledine stated the following: "We've been thinking of state surveillance for years because of our work in places where journalists are threatened. Tor's anonymity is based on distributed trust, so observing traffic at one place in the Tor network, even a directory authority, isn't enough to break it. Tor has gone mainstream in the past few years, and its wide diversity of users - from civic-minded individuals and ordinary consumers to activists, law enforcement, and companies - is part of its security. Just learning that somebody visited the Tor or Tails website doesn't tell you whether that person is a journalist source, someone concerned that her Internet Service Provider will learn about her health conditions, or just someone irked that cat videos are blocked in her location. Trying to make a list of Tor's millions of daily users certainly counts as wide scale collection. Their attack on the bridge address distribution service shows their "collect all the things" mentality - it's worth emphasizing that we designed bridges for users in countries like China and Iran, and here we are finding out about attacks by our own country. Does reading the contents of those mails violate the wiretap act? Now I understand how the Google engineers felt when they learned about the attacks on their infrastructure.”
- Teil 1: NSA targets the privacy-conscious
- Teil 2: The Tor Project - anathema to the NSA
- Teil 3: Servers in Germany targeted
- Teil 4: Simple web searches are suspicious
- Teil 5: NSA: In strict accordance with the rule of law