Investigations in the so-called darknet: Law enforcement agencies undermine Tor anonymisation
The Tor network is considered the most important tool for surfing the internet anonymously. Law enforcement agencies have apparently begun to infiltrate it in order to expose criminals. They have been successful in at least one case.
Law enforcement agencies in Germany sometimes have servers in the Tor network surveilled for months in order to deanonymise Tor users. Sites on the so-called darknet are particularly affected. This is revealed by research conducted by the ARD political magazine Panorama and STRG_F (funk/NDR). According to the research, the data obtained during surveillance is processed in statistical procedures in such a way that Tor anonymity is completely cancelled out. Reporters from Panorama and STRG_F were able to view documents that show four successful measures in just one investigation. These are the first documented cases of these so-called ‘timing analyses’ in the Tor network worldwide. Until now, this was considered practically impossible.
Largest anonymisation network in the world
Tor is the world's largest network for anonymous internet browsing. Tor users route their connection via servers, known as Tor nodes, to disguise what they are doing: Using the Tor browser, they can navigate websites on the internet anonymously or access pages on the so-called darknet. There are currently almost 8,000 Tor nodes in operation in around 50 countries. Around two million people use it every day.
It is popular among journalists and human rights activists, especially in countries where the internet is censored. In Germany too, media organisations, including NDR, operate anonymous ‘mailboxes’ on the Tor network so that whistleblowers can transmit data securely. Deutsche Welle, for example, has made its website accessible on the darknet in order to escape censorship in some countries.
Infiltration of the Tor network
However, anonymity also attracts criminals who use Tor to carry out cyber attacks or operate illegal marketplaces on the darknet, for example. For years, Tor has been a technically almost insurmountable hurdle for investigative authorities. Research by Panorama and STRG_F has now revealed that they have apparently recently expanded their strategy to overcome Tor. This requires surveilling individual Tor nodes, sometimes for years.
The logic behind the measure, which experts call ‘timing analysis’: The more nodes in the Tor network are surveilled by the authorities, the more likely it is that a user will attempt to disguise their connection via one of the monitored nodes. By timing individual data packets, anonymised connections can be traced back to the Tor user, even though data connections in the Tor network are encrypted multiple times.
‘Ricochet’ chat service as a trap
According to research by Panorama and STRG_F, the German Federal Criminal Police Office (BKA) and the Public Prosecutor General's Office in Frankfurt am Main were successful with this method: in the investigation against the paedocriminal darknet platform ‘Boystown’, they succeeded several times in identifying Tor nodes that were used by one of the people behind the operation to anonymise themselves.
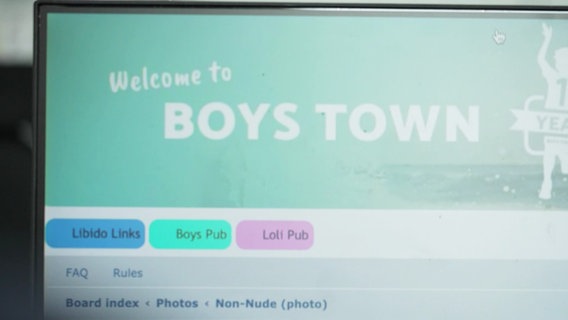
For example, the BKA twice investigated Tor nodes used by platforms operated by the then ‘Boystown’ administrator Andreas G. to connect to the Tor network. This involved, for example, a chat in which leading members of various paedocriminal forums exchanged information. On two occasions, it was also possible to identify so-called ‘entry servers’ from the chat service ‘Ricochet’, which G. used - it was a breakthrough for the BKA. For the final identification, the district court (Amtsgericht) of Frankfurt am Main finally obliged the provider Telefónica to find out from all o2 customers which of them connected to one of the identified Tor nodes. The investigation led to the arrest of Andreas G. in North Rhine-Westphalia. In December 2022, he was sentenced to many years in prison. The judgement is not yet final.
Increasing international cooperation
The BKA received crucial information in the ‘Boystown’ case from the Netherlands. Apparently no coincidence: In Germany, the Netherlands and the USA the most Tor nodes are operated. The responsible public prosecutor's office in Frankfurt am Main said on enquiry that it would neither confirm nor deny a ‘timing analysis’ in the ‘Boystown’ case. The Federal Criminal Police Office (BKA) also declined to comment.
However, reporters from Panorama and STRG_F were able to speak to people who have independent knowledge of the widespread monitoring of such Tor servers. The number of surveilled Tor nodes in Germany is said to have risen sharply in recent years. The recorded data also suggests that these are likely to be used for ‘timing analyses’. Experts who were able to view research documents from Panorama and STRG_F independently confirmed the research results. Matthias Marx, one of the spokespersons for the Chaos Computer Club (CCC), explains: ‘The documents in conjunction with the information described strongly suggest that law enforcement authorities have repeatedly and successfully carried out timing analysis attacks against selected Tor users for several years in order to deanonymise them.’
A major blow for the Tor Project
The revelations are a major blow for the Tor Project. The non-profit organisation based in the USA, which aims to ensure the maintenance of the anonymisation network, stated on request that it was not aware of any documented cases of ‘timing analysis’. So far, however, there was nothing to suggest that the Tor browser had been attacked, a spokesperson of the organization said: ‘Tor users can continue to use Tor Browser to access the web securely and anonymously.’ A representative of ‘Ricochet’, which is now called ‘Ricochet Refresh’, said that she was not aware of any other cases of deanonymized users. The software has been improved in recent years and is one of the safest ways to communicate online, she said.
Matthias Marx from the CCC warns of the consequences of the measure: ‘This technical possibility exists not only for German law enforcement authorities to prosecute serious criminal offences, but also for unjust regimes to persecute opposition members and whistleblowers. The Tor project is therefore now under pressure to improve anonymity protection.’




